Beware: Your Cloud Server May Have Some IP Related Baggage
Cloud based servers are great. You can quickly fire up new instances to scale up a web site or just to make deployment easier.
However, your new cloud server may not be as clean and new as you expect. The problem is that IPv4 addresses are in short supply and your cloud server provider will maintain a pool of addresses that get recycled when a cloud server is destroyed. So when you create a new cloud server, the IP address assigned to it may have some baggage from its previous owner.
We ran into this when we deployed a major update of our site to a new server. Not long after deployment we got a Google Alert about the presence of HttpWatch related content at site with a strange domain name – let’s say malwarecentral.com. The weird thing was that this site was an exact replica of our site:
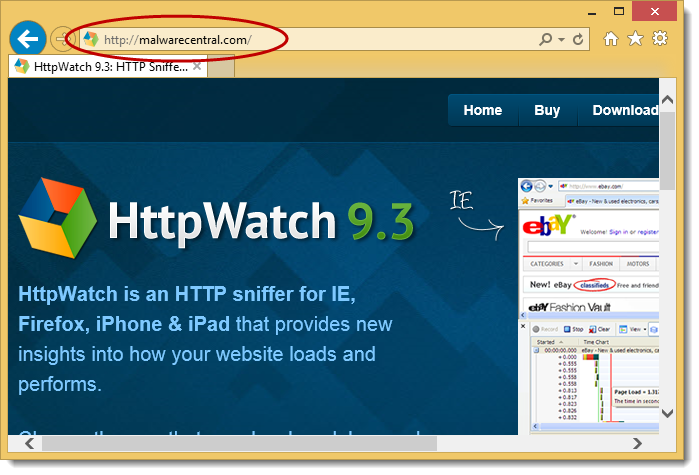
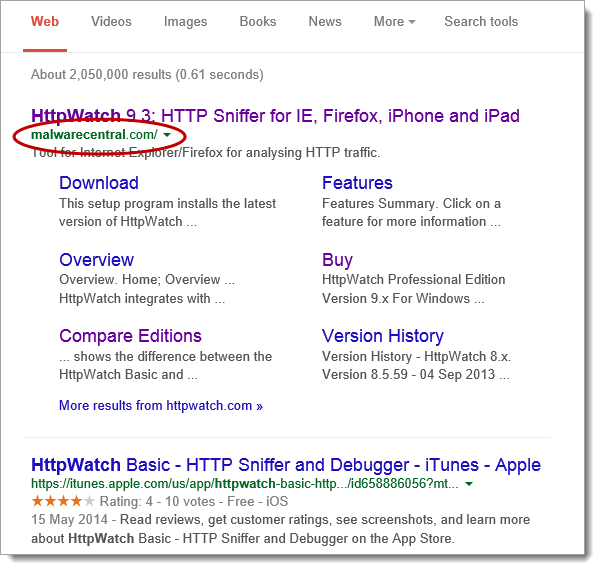
The site must have had a high page rank in Google, perhaps through dubious SEO techniques. If we searched for ‘HttpWatch’ the site appeared as one of the first search results:
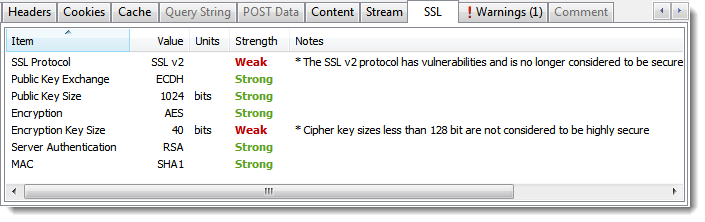
Using HttpWatch we checked the IP address used by the site and found that it was the same as our latest cloud server:
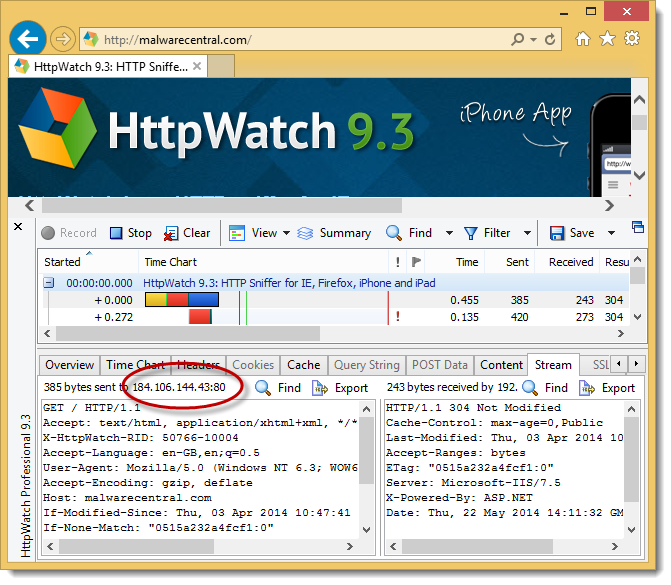
It wasn’t a copy of our site it was an existing DNS entry that was pointing at the same IP address as our server.
How could this have happened? The scenario may have gone something like this:
- A stolen credit card was used to register a domain name (e.g. malwarecentral.com) and setup an account at the cloud server provider.
- A DNS entry for the domain was setup for the new cloud server
- The cloud server may have been used for phishing, malware distribution or some other questionable activity
- The cloud server provider gets a chargeback on the credit card used to setup the account. The account is shutdown and all cloud servers related to that account are destroyed.
- The IP address of the server is returned to the provider’s pool of IPV4 addresses. The DNS entry for malwarecentral.com may have been created at another provider and was not deleted.
- We happened to get this IP address when we created a new cloud server and the DNS entry for malwarecentral.com was still using this IP address.
Tip: Never Use Default Binding For Your Web Site
A simple way to avoid old DNS entries referring to your site is to remove the default binding that allows any hostname to be used. In IIS the entry looks like this:
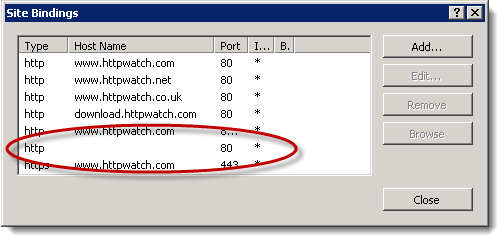
Once it is removed only requests containing the hostnames that you specify will be able to load pages.
Conclusion
There may be other consequences to reusing an IP address on your cloud server. It may have been black listed by email systems if it was sending spam and it could be blocked from other web sites or services if it was engaged in Denial Of Service (DOS) attacks or hacking attempts.
This problem doesn’t exist with IPv6 because it has such a large address space that the cloud server provider could create a new address for every server instance without ever having to reuse addresses from deleted servers. However, in today’s world where IPv4 dominates it’s worth remembering that your cloud server’s IP address may come with some baggage.