One of the interesting new features in Google’s Chrome browser is the use of one Windows process per site or tab. This helps to enforce the isolation between tabs and prevents a problem in one tab crashing the whole browser.
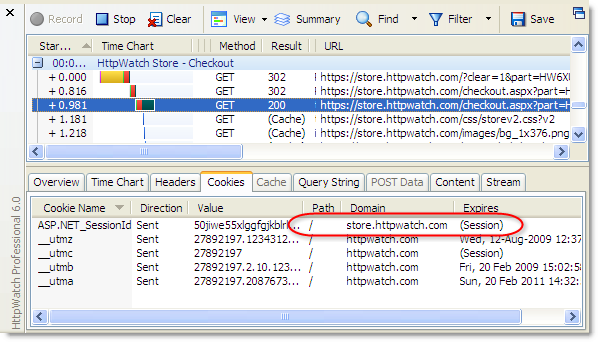
In comparison, Firefox seems to have a simplistic process model on Windows. It doesn’t matter how many tabs or windows you open, or how many times you start Firefox – by default you get one instance of firefox.exe:
In Internet Explorer you can create a separate instance of the browser process just by starting another copy of iexplore.exe.
There are advantages to Firefox’s single process model:
- It uses less system resources per tab compared to creating multiple Windows processes.
- Firefox can use fast in-process data access and syncronization objects when it interacts with the history, cookie and cache data stores.
However, the lack of isolation means that if anything causes a page to crash, you’ll lose all your Firefox tabs and windows. This is mitigated to some degree by Firefox’s ability to restart the browser and reload the set of pages displayed in the previous session.
So what do you do if you are developing an add-on for Firefox or you want to run automated tests in Firefox whilst still using Firefox to browse in the normal way?
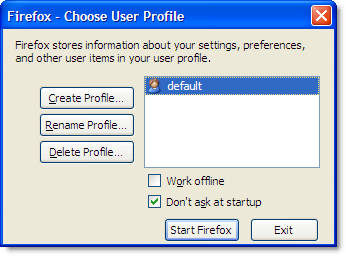
In Firefox, multi-process support is provided through the use of profiles. When Firefox is installed, you automatically get one default profile that contains user settings, browsing history, the browser cache and persistent cookies. Additional profiles can be created using the Firefox Profile Manager.
The Profile Manager is built into Firefox and is started by running this command in Start->Run:
firefox -P -no-remote
The -P flag indicates that the Profile Manager should be started and the -no-remote flag indicates that any running instances of Firefox should be ignored. If you run without this flag and you have already started Firefox, the command will simply open a new Firefox window without displaying the Profile Manager.
The Profile Manager has a simple user interface that allows you to create, delete and rename profiles:
You can start Firefox in a non-default profile by using the following command line:
firefox -P <myprofile> -no-remote
For example, if you created a new profile called AutoTest:
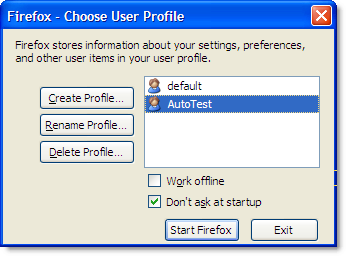
You could set up a shortcut like this to start Firefox in the AutoTest profile:
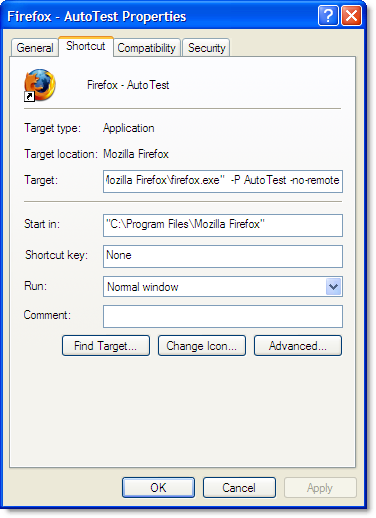
Each profile uses its own copy of the firefox.exe process, as well as its own settings, browser cache, history and peristent cookies. This provides more isolation than you would achieve by running multiple processes in IE. You can even separately enable or disable add-ons like Firebug or HttpWatch in each profile.
Internet Explorer’s cache and persistent cookies are maintained on a per user basis making it difficult to run separate instances with their own storage and settings. With Firefox you simply use different profiles. For example, you could use your default profile for normal browsing and have a separate profile to use for another purpose such as automated testing:
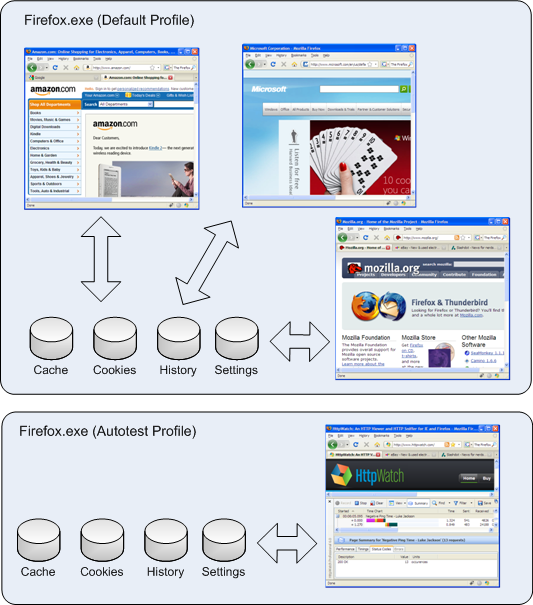
The HttpWatch automation interface in version 6.0 supports the use of profiles with Firefox. The profile name can be passed to the Attach and New methods of the Firefox plugin object. Passing an empty string indicates that you want to use the default profile.
Here’s a modified version of the page load test that we previously featured. It’s written in C# and uses a non-default profile to run the test:
// Set a reference to the HttpWatch COM library
// to start using the HttpWatch namespace
using HttpWatch;
namespace EmptyCacheTest
{
class Program
{
static void Main(string[] args)
{
string url = "http://www.httpwatch.com";
string profileName = "AutoTest";
Controller controller = new Controller();
// Create an instance of Firefox in the specified profile
Plugin plugin = controller.Firefox.New(profileName);
// Clear out all existing cache entries
plugin.ClearCache();
plugin.Record();
plugin.GotoURL(url);
// Wait for the page to download
controller.Wait(plugin, -1);
plugin.Stop();
// Find the load time for the first page recorded
double pageLoadTimeSecs =
plugin.Log.Pages[0].Entries.Summary.Time;
System.Console.WriteLine( "The empty cache load time for '" +
url + "' was " + pageLoadTimeSecs.ToString() + " secs");
// Uncomment the next line to save the results
// plugin.Log.Save(@"c:\temp\emptytestcache.hwl");
plugin.CloseBrowser();
}
}
} |
// Set a reference to the HttpWatch COM library
// to start using the HttpWatch namespace
using HttpWatch;
namespace EmptyCacheTest
{
class Program
{
static void Main(string[] args)
{
string url = "http://www.httpwatch.com";
string profileName = "AutoTest";
Controller controller = new Controller();
// Create an instance of Firefox in the specified profile
Plugin plugin = controller.Firefox.New(profileName);
// Clear out all existing cache entries
plugin.ClearCache();
plugin.Record();
plugin.GotoURL(url);
// Wait for the page to download
controller.Wait(plugin, -1);
plugin.Stop();
// Find the load time for the first page recorded
double pageLoadTimeSecs =
plugin.Log.Pages[0].Entries.Summary.Time;
System.Console.WriteLine( "The empty cache load time for '" +
url + "' was " + pageLoadTimeSecs.ToString() + " secs");
// Uncomment the next line to save the results
// plugin.Log.Save(@"c:\temp\emptytestcache.hwl");
plugin.CloseBrowser();
}
}
}
![]() March 9, 2009 in
HttpWatch
March 9, 2009 in
HttpWatch  Version 6.1 is now available for download. It contains fixes, improvements and the following new features:
Version 6.1 is now available for download. It contains fixes, improvements and the following new features: