Google Has Given HTTPS A Huge Boost
![]() July 7, 2014 in
HTTPS , HttpWatch , Optimization , SPDY , SSL
July 7, 2014 in
HTTPS , HttpWatch , Optimization , SPDY , SSL
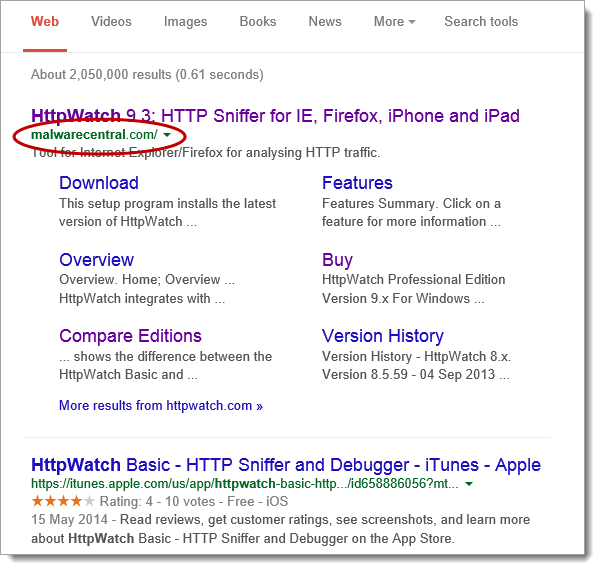
For a while now there’s been talk of Google favoring secure HTTPS pages in its results. We just noticed this week that any Google searches for content on our web site now return secure HTTPS URLs instead of HTTP:
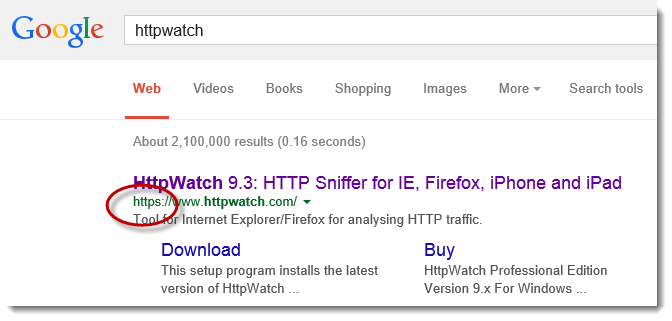
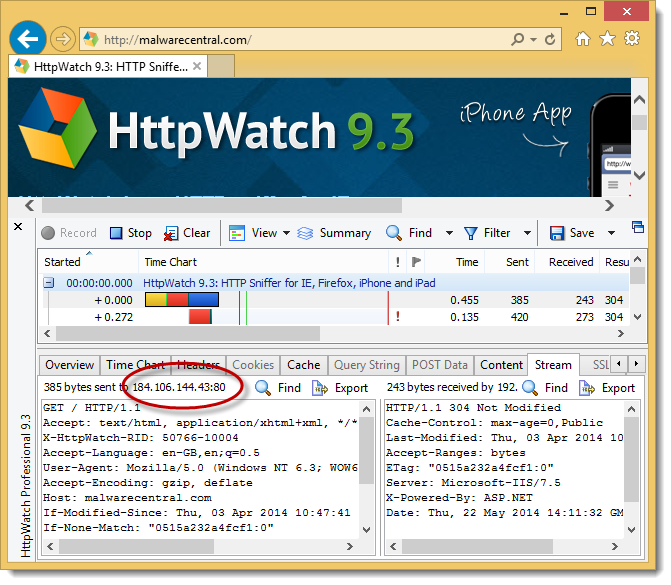
It’s not clear when this happened but a quick check on our web server shows that nearly 75% of all connections were HTTPS:
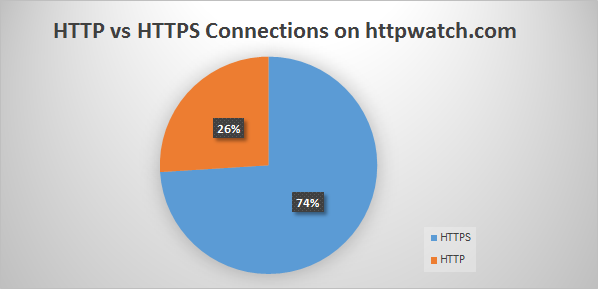
Only a year or so ago HTTPS connections only made up about 10% of all connections. The percentage of HTTPS URLs being used is only going to increase as more people find HTTPS based results on Google and then share them in web pages, emails and social media.
So if your site supports based HTTP and HTTPS then HTTPS is now the most important in terms of optimising performance. The good news if that HTTPS isn’t necessarily much slower than HTTP and may be even faster if you support SPDY.
UPDATE July 7, 2014: There’s been a lot of interest in this post and some people have been jumping on the SEO implications of this. We’re not implying that your site will get ranked higher than other sites if you have HTTPS. What we’re saying is that if your site has both HTTP and HTTPS versions of the same content that Google will now return an HTTPS link. The biggest implication is that if you support HTTPS most of traffic will now be using HTTPS rather than HTTP.
UPDATE August 6, 2014 – Google has confirmed that HTTPS will be used as a ranking signal in Google Search.