This blog post isn’t about HTTP performance or HttpWatch itself but you may find it useful if you advertise a software product with Google Adwords. Hopefully, you’ll also find our conversation with Google amusing!
What Happened ?
We received an email like this:
Subject: Your AdWords account: Ads not running due to AdWords Advertising Policies
Hello,
We wanted to alert you that one of your sites violates our advertising policies. Therefore, we won’t be able to run any of your ads that link to that site, and any new ads pointing to that site will also be disapproved.
Here’s what you can do to fix your site and hopefully get your ad running again:
1. Make the necessary changes to your site that currently violates our policies:
Display URL: httpwatch.com
Policy violation: Unwanted software
Details & instructions:
https://support.google.com/adwordspolicy/answer/50423?hl=en_GB
…
At first it looked like a phishing email as we go to great lengths to ensure that our software is easily uninstalled and that we never mislead anyone into installing it (e.g. bundling with other applications).
After a few checks it was clear that the email was legitimate and that our ads had been dropped from Google search.
The page linked by the email didn’t suggest anything that applied to our software. The two main points were:
- Malicious software or “malware” that may harm or gain unauthorised access to a computer, device or network
- Promotions that violate Google’s Unwanted Software policy
We got in touch with Google Support as there were no obvious violations of their advertising policy.
Our Conversation With Google Support
Here’s a subset of our conversation with Google Support:
Google Support: How can we help you? *
Simtec: We received a ‘Policy violation: Unwanted software’ notification with no detailed explanation of why this occurred. It makes no sense. Our software is only installed when users download and run the setup program. It is uninstalled in the standard way by going to the Windows Control Panel ‘Uninstall Program’ section.
Please can you tell us how we can get our ads re-instated? We’ve been advertising the same software on Adwords for almost 12 years and have spent over a $ 1 million. We are amazed that you would just drop our ads with no pre-warning or at least a decent explanation of the problem
Google Support: Hi there, thanks for chatting in today! I have your question here, so just give me a moment to take a look
Google Support: Did you make any recent changes to your website or anything?
Simtec: Our website was updated in February to make it mobile friendly
Google Support: Hm, but otherwise nothing else?
Simtec: Nothing else. Don’t you have a detailed reason why this occurred?
Google Support: Just one second, let me find the right form. ? I want to see if I can get more visibility for you
Simtec: Frankly, we’re furious that we have spent so much money with Google to have our ads dropped without any details or warning
Google Support: Unfortunately I don’t have control over that right now but I can look into it for you
….
Google Support: I looked through this, and it seemed that one of the issues was a lack of an End User Agreement (EULA)
Simtec: An EULA is displayed by the setup program before installing starts. Also, the end user license agreements are linked to from here http://www.httpwatch.com/buy/orderingfaq.aspx#licensetypes
Google Support: Hmm, They do want it on the download page itself
Simtec: How come there isn’t one here? https://www.google.co.uk/chrome/browser/desktop/
Google Support: Lol
Simtec: No really?
Google Support: That’s a great question
Simtec: Seems like you guys should put our ads back up, apologise and then sort out your policies
…
Google Support: Ah okay, So if you click the download (for Chrome) there’s a popup with the TOS
Simtec: There is when the program (HttpWatch Setup) runs. You can’t install it without agreeing the EULA
Google Support: So after you download it? The install requires a EULA?
Simtec: Yes, the setup will not install anything unless you agree to the EULA. It has an ‘I Agree’ button. We’ve been doing that for more than a decade. Why the change now?
Google Support: I’m not sure when the change occurred, but if we do want to resolve this—we’?ll need to get the EULA there
….
Simtec: The changes (EULA Link) are live at http://www.httpwatch.com/download/
…
Google Support: I have an update from the policy team. They found that the website still does not fully comply:
Website promoting software is required to have the following items present :
Uninstall guidelines should be clearly visible and/or accessible from the download page. The uninstall information must be on the download page itself or accessible from the download page by a relevant link such as “Help”, “Support”, “Uninstall”, “Remove Program/Application”. It should not be located within other pages that are not directly related to uninstall (e.g. privacy policy, terms of service)”
Simtec: We’ve updated the site. If you click the Support link on the download page the first paragraph explains how to uninstall HttpWatch. (i.e. in the standard way through the Control Panel). Is that sufficient to get our ads re-instated?
We checked https://www.google.co.uk/chrome/browser/desktop/ but couldn’t find anything similar there.
…
Google Support: Great news! We’ve re-reviewed your site and determined that the following site complies with our Advertising Policies
What did we change?
The two changes to make our site comply with Google policies was a link to the EULA next to the download link:

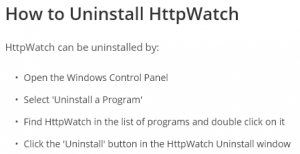
On our support page we included instructions on how to uninstall a Windows program:
Conclusion
If this happens to you the fastest way to get the problem resolved seems to be by using a chat window with Google Support.
Fortunately, our ads were back up after a couple of days and at least Google wasn’t trying to stop us using hyperlinks! See Google Bans Hyperlinks .