HttpWatch iOS App Now Supports Password Managers and other App Extensions
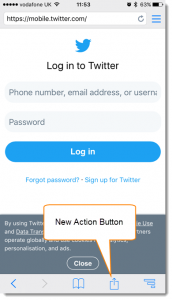
The latest update (version 11.0.15) of the HttpWatch iOS app has a new share sheet that can be opened from the browser window:
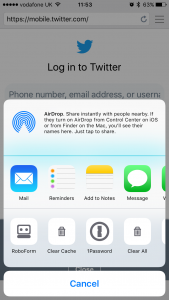
The top row of icons allow sharing the current URL with standard apps such as Mail and iMessage while the bottom row includes built-in actions and extensions from other apps:
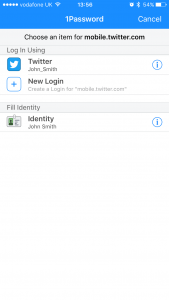
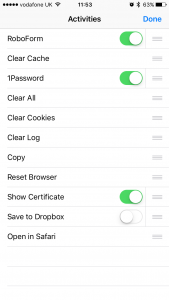
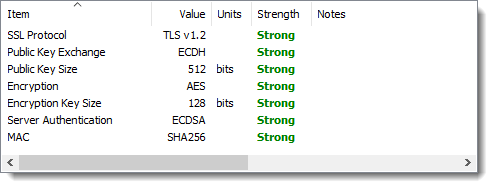
If you already use a password manager app such as 1Password or Roboform you can now use it to fill in user names and passwords on web pages within the HttpWatch app. The 1Password app also supports filling in identity information such as name, address, credit card details, etc:
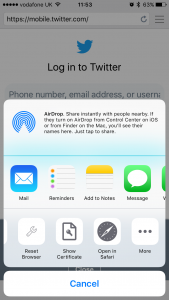
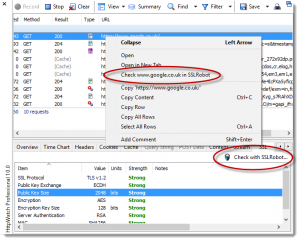
Other apps such as certificate checkers can also be used from the share sheet and we’ve included several built-in actions such as Reset Browser, Clear Cache and Open in Safari.
By selecting More… you can control which actions appear and their order in the share sheet: