New Password Masking Feature in HttpWatch 10
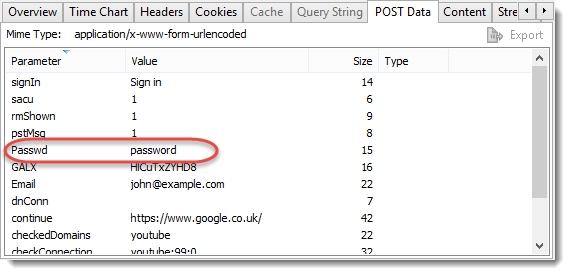
One of the commonly voiced concerns with previous versions of HttpWatch was that the log file may record passwords used to log into web based systems. If you looked at the POST tab after logging into a site you would usually be able to find the password in clear text:
HttpWatch 10 for Windows and iOS now includes a feature that will mask out the passwords for most commonly used login pages. It works by looking for form submits where the POST parameter name suggests a password or some other form of sensitive data. Any POST field that meets the matching criteria will have each character of input replaced with an asterisk (*).
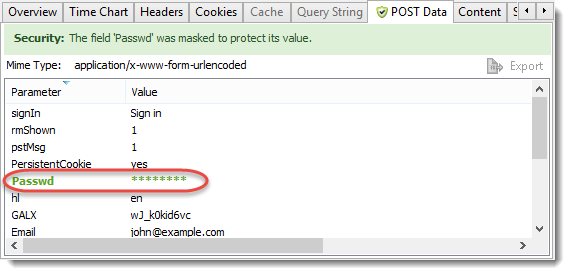
For example, here’s the POST Data tab in HttpWatch showing a login to a Google account:
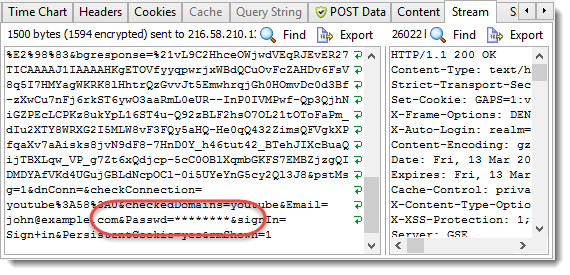
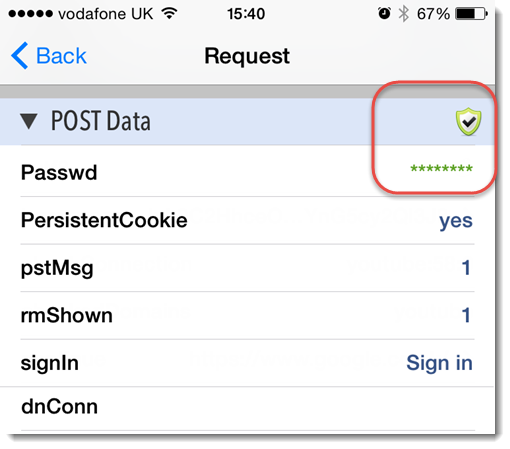
The password characters have been masked out and colored in green. The banner and icon on the tab also confirm that password masking has occurred. The masking also applies at the network level in the Stream tab:
Although the actual password was sent to the web server, HttpWatch only records the masked version of the password in the Stream tab.
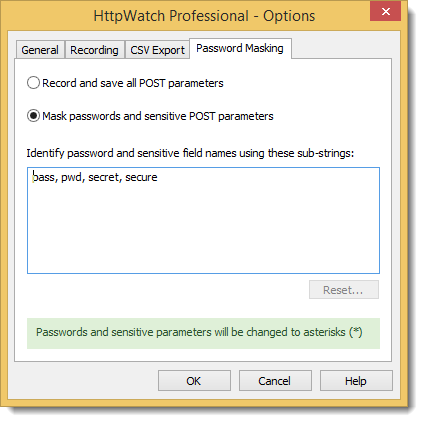
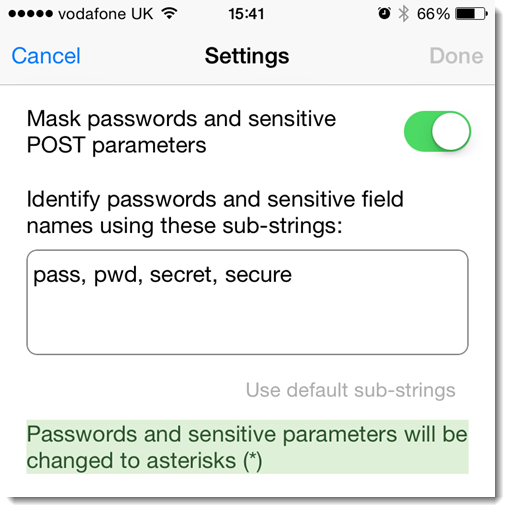
The criteria used to select POST fields for masking is based on checking whether a list of sub-strings occur in the name. The default sub-strings of ‘pwd’, ‘pass’, ‘secure’ and ‘secret’ catch passwords on most sites but the list is configurable in Tools->Options:
You could change the list if a password field is not being masked or if you want to turn off the feature completely.
The same masking functionality is built into the POST Data section of the iOS app:
and a new Settings view allows the substrings to be modified:
There are still some security related issues to consider when recording and sharing log files:
- The password masking feature doesn’t hide the length of the underlying password as it uses a character for character substitution.
- Cookies used for session management are still recorded in the log file and could be re-used to access the logged in session if they have a long expiration time.
- Content seen in the logged in session is recorded, e.g. html and images
- Query string values are recorded but it’s probably best to not put anything of a security sensitive nature in a URL
However compared to previous versions, the masking of submitted passwords is a significant improvement to security when sharing log files with third parties.