Using SSLRobot 1.2 to Check Proxy Configuration
![]() November 5, 2018 in
HTTPS , Security , SSL , SSLRobot , Uncategorized
November 5, 2018 in
HTTPS , Security , SSL , SSLRobot , Uncategorized
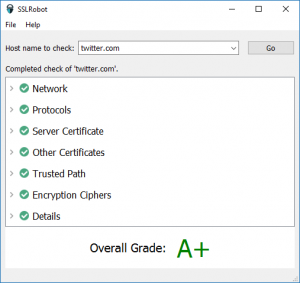
We’ve recently updated our SSLRobot TLS/SSL checking tool with three main changes:
- It now uses the locally installed root CA certificates (Windows or MacOS) to support servers that use custom in-house generated SSL certificates.
- The Network section displays detailed information about the operating system’s proxy configuration.
- It’s free to use with any host name although the extended features such as save, print and email require a license key or an in-app purchase from the Mac App Store.
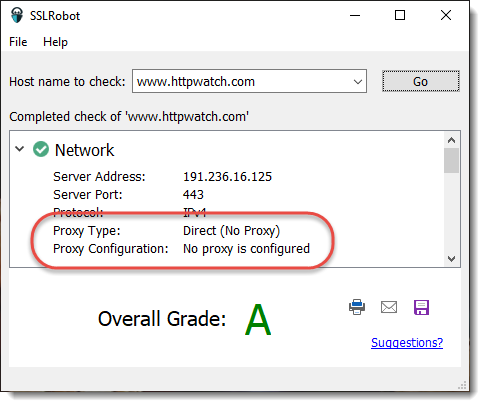
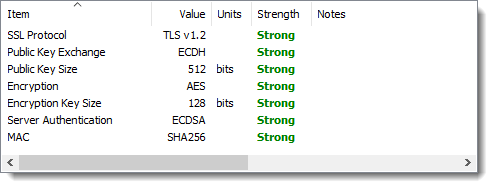
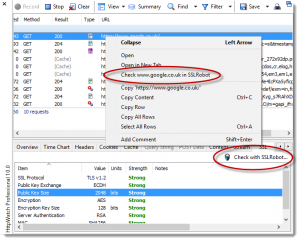
Item 2) means that SSLRobot can be a useful tool for debugging and verifying proxy settings even if you don’t need to check the SSL/TLS configuration. Just type a host name into SSLRobot and expand the Network section to see the system proxy configuration.
When there’s no proxy settings on a Mac or PC you’ll see something like this in the Network section:
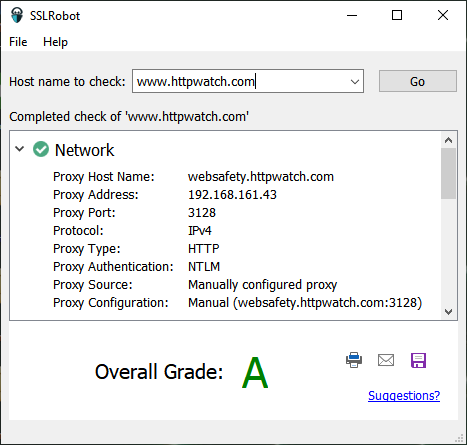
and with a manually configured proxy you’ll see this:
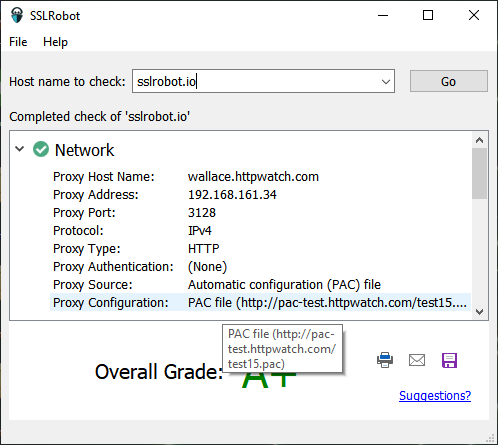
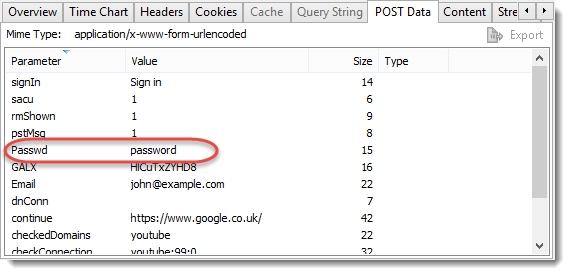
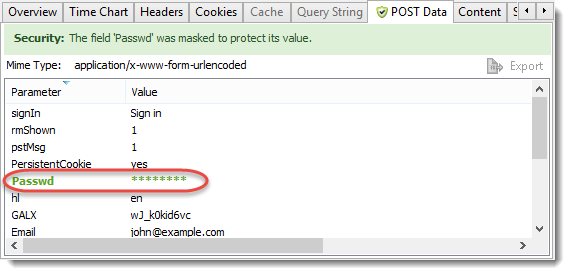
The proxy data fields show how the proxy was configured and in this case that NTLM authentication was used. It also shows if a PAC (proxy auto config) file was used to specify the proxy on a per host basis:
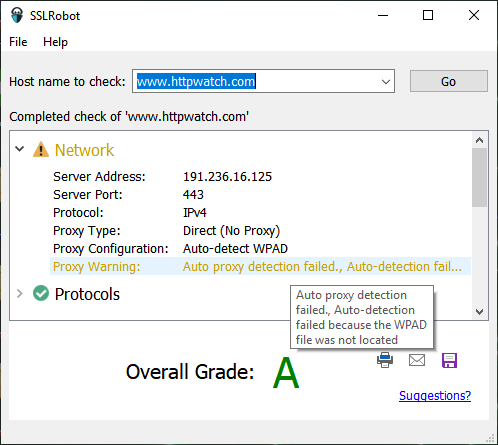
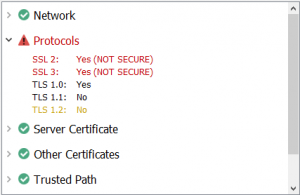
If SSLRobot detects any potential problems it displays a warning, e.g. the WPAD file location could not be found when using proxy auto-detection :